Toggle navigation
Home
安装部署
Archives
Tags
Certbot
ssl证书
2019-05-06 06:51:53
59
0
0
louyj
ssl证书
#Install Certbot is packaged in EPEL (Extra Packages for Enterprise Linux). To use Certbot, you must first enable the EPEL repository. After doing this, you can install Certbot by running: sudo yum install certbot #Generate cert Certbot supports a number of different “plugins” that can be used to obtain and/or install certificates. Since your server architecture doesn't yet support automatic installation you should probably use the certonly command to obtain your certificate. certbot certonly --webroot -w /var/www/example -d example.com -d www.example.com -w /var/www/thing -d thing.is -d m.thing.is This command will obtain a single cert for example.com, www.example.com, thing.is, and m.thing.is; it will place files below /var/www/example to prove control of the first two domains, and under /var/www/thing for the second pair. Currently it is possible to perform a DNS validation also with the certbot LetsEncrypt client in the manual mode. Automation is also possible (see below). You can either perform a manual verification - with the manual plugin. certbot -d bristol3.pki.enigmabridge.com --manual --preferred-challenges dns certonly Certbot will then provide you an instructions to manually update a TXT record for the domain in order to proceed with the validation. Please deploy a DNS TXT record under the name _acme-challenge.bristol3.pki.enigmabridge.com with the following value: 667drNmQL3vX6bu8YZlgy0wKNBlCny8yrjF1lSaUndc Once this is deployed, Press ENTER to continue Once you have updated DNS record, press Enter, certbot will continue and if LetsEncrypt CA verifies the challenge, certificate is issued as normally. 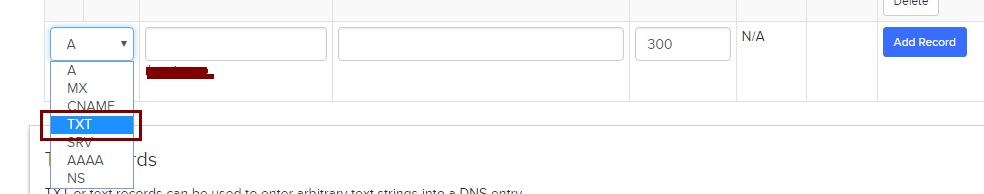 #Automating renewal Certbot can be configured to renew your certificates automatically before they expire. Since Let's Encrypt certificates last for 90 days, it's highly advisable to take advantage of this feature. You can test automatic renewal for your certificates by running this command: certbot renew --dry-run or certbot renew --quiet or certbot renew
Pre:
Corvus+Redis Cluster
Next:
Open365环境部署
0
likes
59
Weibo
Wechat
Tencent Weibo
QQ Zone
RenRen
Submit
Sign in
to leave a comment.
No Leanote account?
Sign up now.
0
comments
More...
Table of content
No Leanote account? Sign up now.